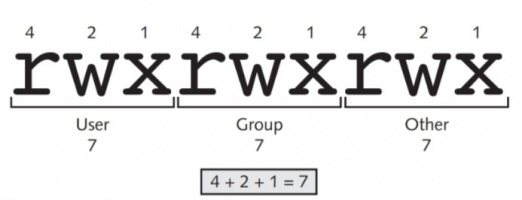Centos Permissions
View your current username
whoami
View your group membership
groups
Change Group
chgrp sys file1 chgrp -R sys Desktop
Chown changes ownership and group ownership of a file
chown user1.root file1 chown -R user1.root Desktop
Umask set new files created with these permissions
umask 022 # if was rw-rw-rw- # with umask of 022 it would take away the w for group and other (-2) but leaves the user (0) alone
A user who does not have the execute permission to a directory is prevented from listing the directory’s contents, adding and removing files, and working with files and subdirectories inside that directory, regardless of what permissions the user has to them. In short, a quick way to deny a user from accessing a directory and all of its contents in Linux is to take away the execute per- mission on that directory. Because the execute permission on a directory is crucial for user access, it is commonly given to all users via the other category, unless the directory must be private.
To change the mode of file1 to rw-r--r--, you must add the write permission to the user of the file, add the read permission and take away the write permission for the group of the file, and add the read permission and take away the execute permission for other.
chmod u+w,g+r-w,o+r-x file1
If the permissions to be changed are identical for the user, group, and other categories, you can use the “a” character to refer to all categories.
chmod a+x file1
All of the aforementioned chmod examples use the symbols listed in Table 4-5 as the criteria used to change the permissions on a file or directory. You might instead choose to use numeric criteria with the chmod command to change permissions. All permissions are stored in the inode of a file or directory as binary powers of two:
- read=2^2=4
- write=2^1=2
- execute=2^0 =1
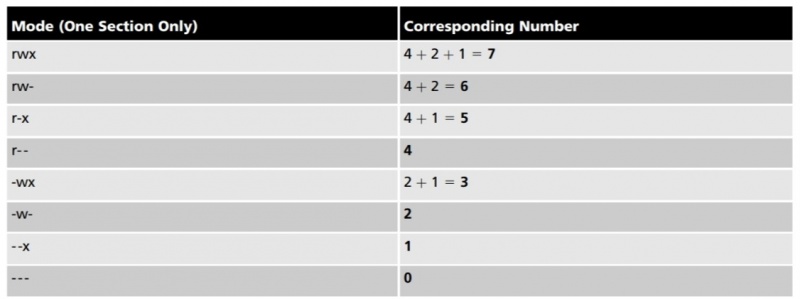
Thus, the mode of a file or directory can be represented using the numbers 421421421 instead of rwxrwxrwx. Because permissions are grouped into the categories user, group, and other, you can then simplify this further by using only three numbers, one for each category that represents the sum of the permissions, as depicted in Figure 4-4. Similarly, to represent the mode rw-r--r--, you can use the numbers 644 because user has read and write (4 þ 2 = 6), group has read (4), and other has read (4). The mode rwxr-x--- can also be represented by 750 because user has read, write, and execute (4 þ 2 þ 1 = 7), group has read and execute (4 þ 1 = 5), and other has nothing (0). Table 4-6 provides a list of the different permissions and their corresponding numbers.
New files are given rw-rw-rw- by the system when they are created (because execute should not be given unless necessary), and new directories are given rwxrwxrwx by the system when they are created. These default permissions are too permissive for most files, as they allow other full access to directories and nearly full access to files. Hence, a special variable on the system called the umask (user mask) takes away permissions on new files and direc- tories immediately after they are created. The most common umask that you will find is 022, which specifies that nothing (0) is taken away from the user, write permission (2) is taken away from members of the group, and write permission (2) is taken away from other on new files and directories when they are first created and given permissions by the system.
The owner of the file (user1) has read and write permission, the group (acctg) has read and write permission, and everyone else has no access to the file. Now imagine that you need to give read permission to the bob user without giving permissions to anyone else. The solution to this problem is to modify the ACL on the doc1 file and add a special entry for bob only. This can be accomplished by using the following setfacl (set file ACL) command: [root@server1 ~]# setfacl -m u:bob:r-- doc1 [root@server1 ~]# _ The –m option in the command above modifies the ACL, and you can use g instead of u to add an additional group to the ACL. Now, when you perform a long listing of the file doc1, you will see a + symbol next to the mode to indicate that there are additional entries in the ACL for this file. To see these additional members, simply use the getfacl (get file ACL) command
getfacl doc.txt
To remove all extra ACL assignments on the doc1 file, simply use the –b option to the setfacl comman
setfacl –b doc
Filesystem Attributes
To see the filesystem attributes that are currently assigned to a file, you can use the lsattr (list attributes) command, as shown here for the doc1 file:
[root@server1 ~]# lsattr doc1 -------------e-- doc1 [root@server1 ~]# _
By default, all files have the e attribute, which writes to the file in “extent” blocks (rather than immediately in a byte-by-byte fashion). If you would like to add or remove attributes, you can use the chattr (change attributes) command. The following example assigns the immutable attribute (i) to the doc1 file and displays the results:
[root@server1 ~]# chattr +i doc